Mfi’s Risk Assessment
Question :
You are given a fictional scenario above describing security issues affecting organizational assets. You will identify the risks associated with the assets and recommend mitigating procedures. You will prepare a quantitative/qualitative risk assessment to address risk factors on organizational assets. Your final paper will be 15–25 pages long in a Word document (double-spaced with 12-point font) with APA citations for the resources you used in your research and will be graded using the following rubric.
Answer :
Introduction
The CEO of Mortgage Finance, Inc. (MFI) is desiring to outsource all the possible functions and departments of the company. He is of the view that IT Department can be entirely outsourced to external agencies instead of handling it within the company. The Chief Security Officer of the company is concerned over this willingness of the CEO as he feels that outsourcing the IT related activities of the company will negatively impact the integrity, confidentiality, and availability of the company’s data. This may create operational challenges to the company as well as impact the reputation of the company if something undesirable happens. The cause for concern of CSO seems obvious as in the past, the company has faced several security threats. In the past three years, it faced four major successful attacks that compromised security and confidentiality of the customer data. An information security expert has been hired whose role is to evaluate the current security of the company’s infrastructure and systems.
The focus of the current paper is to conduct risk assessment of the company’s security system and recommend possible improvements that can be made by the company to resolve potential critical threats. In addition, the company is desiring to offers its products and services online. This report also covers the aspects about cloud computing security that the company has to take care to ensure that the threat towards the customer database breach is minimized. The report is divided into several key sections covering important aspects related to the assessment.
Asset Inventory Analysis
Considering the given details of MFI’s network infrastructure, it can be said that there are few key devices and systems that are more important than the other. One of the most important device in the entire network is the Oracle Database Server which is the most critical as it stores all the key data related to the company’s transaction. The priority level of 1 can be assigned to it. At present, the cost of one Oracle Enterprise Edition License is $47,500. The next most important device is the Intranet Web Server which can be cost between $30,000 and $1,000,000. The table below shows the monetary value rank assigned to each devices based on the estimated value:
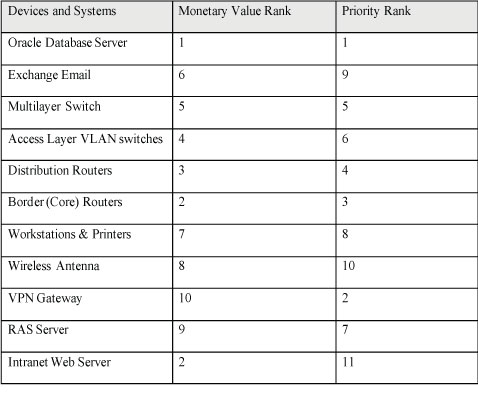
There are few of the most important aspects in the existing system that have to be brought back to proper functioning in the event of catastrophic event or attack. The level of importance can be determined based on the role they play in operation of the company. As known, database server stores all the data of the company. Therefore, without accessibility to this device, company will not be able to do any business transaction. The next aspect is minimum connectivity which can only be allowed through properly operating Border Routers, Distribution Routers, Multilayer and VLAN switches, and the workstations. These are mandatory devices in the network that have to be restored as fast as possible.
Perimeter Security Analysis
There are few internal and external access points that make the system vulnerable to threats. Use of VPN (Virtual Private Network) is one access point that can be used by attackers. Communication through VPN should be encrypted to prevent eavesdropping. This will prevent cybercriminals from monitoring the data transfer. Another is the use of dialup PSTN, which is considered as the least secure. Modem should be made secure, otherwise modem can be accessible from anywhere. The third is the wireless network being used within the company to provide in internet access to the employees in their personal devices. The wireless access point can be tricked by the attackers to reuse an in-use encryption key. With this, the attackers can decrypt the data being sent or received and read without barrier. The best way to ensure that this form of attack does not happen, the IT Department has to regularly update the device. The company should ensure to change the passwords of WIFI access points instead of forgetting to do so and using the default passwords or SSIDs (Sidiropoulos et al, 2012). The another often ignored access points that make network vulnerable is through the devices being used by the employees, whether it is company provided devices or employees’ own devices. Allowing accessibility of secure devices can prevent attacks from this point. These were some of the key access points that lies within or outside the company that should be taken care of in order to ensure perimeter and network security.
Remote Access Infrastructure Evaluation
As far as remote access infrastructure is concerned, the company has current 20 remote facilities, which are connected with the company’s central data processing environment through the use of Virtual Private Network. VPN gateway appliance is used to transmit data from the remote site through the use of VPN tunnel. This VPN connection is being used by the remote site users to get access to the Oracle database for updating customer data. Through the inspection it has been found that no encryption exists in VPN when the data is transmitted from the remote sites to the internal database of the company.
Here, it is suggested that the company should encrypt its Virtual Private Network. The company can use IPSec (Internet Protocol Security) protocol to secure traffic over the IP networks as well as the internet. IPSec can be used for data encryption between various devices whether it is between routers, firewall and router, desktop and server, and router and desktop. There are two sub-protocols within IPSec that provides necessary information needed by VPN for securing the packets (Dandalis & Prasanna, 2004). These sub-protocols are ESP (Encapsulated Security Payload), and Authentication Header (AH). ESP uses symmetric key in order to encrypt the payload of the packet. On the other hand, AH hides some information of the packet by applying hashing operation on the header of the packet till the time it reaches the desired location. The company’s networked devices can utilize one of the two encryption methods given here.
Mobility Security Concerns
It has been found from the case that the company has allowed its employees to use their personal devices such as smartphones, laptops, and USB Drives. The major challenge with these devices are that the company cannot be sure that whether these devices are secure enough. IT Department holds complete control over the devices that are of the company, but they don’t hold complete control over the devices of the employees. Now it is difficult to say which employee is roaming around with their devices infected (Miller et al, 2012). There are two ways to deal with this situation. The first way is to completely ban the use of personal devices within the company premise or through the VPN. However, this may impact the operational efficiency of the organization.
Another approach that can be taken is to focus on the use of authentication technologies and data protection. The company can implement acceptable use policy. Under this policy, employees can be allowed to access only certain data or applications through their personal devices. They cannot be allowed to use USB drives to carry around the company’s data. Further, only those devices can be allowed to connect and gain access that meet minimum level of security controls as specified by the IT Department. Employees will be required to use SSL certificates for the authentication of the devices. The next is that the employees have to give access to their devices to the level where their device data can be wiped in case it gets stolen or lost.
Wireless Vulnerabilities
There are various wireless vulnerabilities that can compromise the data security of the company. The attacker can do wireless sniffing. If the access points are not secured, then attackers can use sniffing tools to gather data being transmitted. This can be resolved if the company uses at least WPA2 encryption (Lashkari et al, 2009). Another vulnerability can be unauthorized computer access. If the wireless network is unsecured and file sharing is also unsecure, then the attackers can easily gain access to the files and directories that are open for sharing. This vulnerability can be resolved if file and folder sharing is denied, and sharing on recognized networks are allowed only. Moreover, along with securing the wireless network, file sharing should be kept disabled when not needed.
Encryption of the wireless data can be successfully used to prevent others from viewing it if somehow they can access to the network. SSID should not be publicized. More it is kept under wraps, better it will be. Installation of firewall on the wireless devices, which is also called host-based firewall, can strengthen the security. The use of host-based firewall increases the security level. Software used on access points should be regularly patched and kept updated. The manufacturers of the wireless access points releases updates and patches for the devices at certain interval whether it is for its firmware of software. The IT Department should regularly check for updates or patches on the manufacturer’s website. Using encrypted VPN to connect with the wireless network is another additional aspect that can significantly help improve the security.
Authentication Protocols and Methodologies
There does not seem to be any authentication protocols being used by the company when it comes to wired network. For the wireless networking, the company is currently using WEP (Wired Equivalent Privacy). As the name suggests, the purpose of the WEP was to be enough secure that it matches its capability to what can be expected from wired LAN. However, WEP is not enough secure. And instead of WEP, WPA is considered more secure (Lashkari et al, 2009). The aim of WPA is to provide encryption of wireless data which is also strong in comparison to the WEP. Further, there are no strong policies that could guide the use of personal devices by the employees. Employees can bring their devices whether it is their laptop, mobile phones, or USB Drive and can use unhindered throughout the organization. This has some serious implications. As stated earlier, it would be difficult to know whose device is carrying viruses and spyware. Therefore, it is important that the authentication of the devices should be done as well. There should be some methodologies in place that can ensure that the system is secure before it connects with the network. The employees who desire to use their devices have to get their device verified through IT Department for approval. There are various authentication methods such as PAP, MS-CHAP, EAP, and others that can be used by the company.
Web System Protocols and Vulnerabilities
Intranet server is generally used within the organization. Therefore, it often stays out of threat if it does not connect with the internet. However, it is not the case of the company. The internet is being used in the middle to connect the intranet of the company to all the remote sites. This increases the vulnerability. For the case of the intranet web applications, the company can use the Windows Authentication system for authentication purposes (Del 2018). Windows Authentication will ensure that the users do not require additional steps of creating login form in the web applications. Moreover, it will also not require the end users for manual entry of the username and passwords to operate the applications. They can easily operate the applications without requiring an additional step. So here it can be said that this system not only increases the security and reduces vulnerability, it also reduces the time consumed by users to login into the application. So it somewhat adds to the efficiency.
Cloud Computing Environment Design
Cloud computing is the need of the hour. Customers are coming online and in order to meet their demand to use the services through online medium, it is important that the company should also start providing its services through online medium. However, as with the case with all other channels, the company is also concerned about the security of the data over the cloud environment. When it comes to data storage over cloud, it often bugs the decision makers regarding security (Almorsy et al, 2016). There are various risks associated with the storage of data in the cloud or providing service to the customers through the use of cloud computing environment. The first issue that can occur is regarding the loss or damage caused to the data by the service provider itself or through their staff members. Another challenge can be disclosure or access of information stored in the cloud without asking for permissions. The third challenge can be possibility of activities undertaken by external parties with the intent to steal data or infect it with viruses. Another problem can arise if the cloud computing provider is not using security practices that are of acceptable standard. These are some of the key challenges that can deter the decision maker from deciding that whether they should go with the cloud computing option.
In order to ensure that the company gets appropriate service from the cloud computing service provider, it has to conduct thorough due diligence and ensure that the service provider uses secure channels to receive and transfer the data. Further, data transfer should take place within the allowed jurisdiction so that necessary legal actions can be taken if need be. Further, having a written contract with the service provider can further help secure the service. A service level agreement is considered mandatory in this scenario.
In order to ensure security of the data, it should be ensured that the data are encrypted whether it is in rest, in motion, or in process. SSL security can be used to secure the data in motion.
Asset Vulnerabilities and Impacts
There are various assets that are being used by the company to run the whole networking. The first and major asset that the company needs protection and is vulnerable to external threat is Oracle database server. It has been found through the past history of the company that the database server had been attacked in the past as well. The database server contains all the information related to the customers of the company. If this data is compromised, then the company will not only lose businesses, it will also lose its reputation in the market. If the data gets into the hands of the competitors, then the company may lose future customers to the competitors. Moreover, as the reputation is what attracts or repels the customers, therefore, in the case of data theft from the server, the company is very likely to lose the trust of its customers and they may not want to share their information with the company. Therefore, it can be said that this aspect can hugely impact the company. Another key asset is the workstations being used within headquarter of the company and the workstations at the remote sites. All these workstations are likely to contain some amount of data related to the customers, albeit in fragmented form. These data can be stolen as well if the workstations are not secure. This will also impact the reputation of the company if words get out. Further, it can be said that the company is using insecure VPN network to transfer data (Singh & Gupta, 2016). Attackers can eavesdrop and steal data and sell it to the competitors. There are other devices within the company that can be compromised as well but at the end, the impacted aspect of the company will be stealing of data. Some other vulnerabilities are use of Dial up PSTN, and use of wireless network within the company premise and allowing the staff members to use their own devices.
Quantitative and Qualitative Risks Assessment
In the earlier section, the monetary and priority values of the asset inventory have been listed in a table. Based on that it can be said that there are certain devices in use within the company that require special attention in order to ensure that the data of the company stays protected and it does not harm its reputation. The Oracle Database Server is the one that is most vulnerable in the company, and very important as well (Jing-wei et l, 2019). On the priority aspect it comes at the top. Moreover, it also costs good amount for the company to purchase and install. Here, it can be said that the data being stored in this device is very valuable as the future of entire organization depends on this device alone. If it wiped out or everything is stolen from here, then it would be difficult to state the future of the business. The case does not mention whether the company is keeping any backup of the data stored on this server. Here, if it is not doing so, then it is makes it more critical to resolve this aspect. From the risk point of view, it can be clearly indicated as most risky asset that the company needs to pay attention to.
Now coming to the second most important aspect of the network of the company, which is the use of VPN network. It also costs a fortune to set up all the switches and VLANs, but without the use of encryption in VPN, everything will be compromised. Risk posed by this aspect is also too high for the company, and the company needs to pay attention towards it. Using encryption in VPN will not cost much, but with its absence, it will incur heavy cost to the company’s future. So this aspect can also be placed on the high priority list and considered risky.
Another aspect is the use of Wireless network within the company premise. Wireless is using WEP which is not secure enough in comparison to WAP. Wireless can be accessed by individuals with malicious intent from outside the organization and manipulate it for their own benefit by compromising the entire network. In addition to this, the BOYD facility further complicates the process and makes it more risky.








